Let's define vulnerability first. What is vulnerability? Well, according to ISO 27001, vulnerability is a weakness of an asset or control that could potentially be exploited by one or more threats. A threat is defined as any potential cause of an unwanted incident, which may result in harm to a system or organization. The main objective of Cyber Security is to address threats to information assets.
How about categorization? Vulnerabilities also have categorization and categorizing vulnerabilities helps to better understand their nature, potential impact, and the specific security measures required to address them effectively.
Software Vulnerabilities: These are flaws or weaknesses in software code that can be exploited by attackers to gain unauthorized access, execute arbitrary code, or cause a system to crash. Common vulnerabilities include buffer overflows, SQL injection, and cross-site scripting (XSS).
Operating System Vulnerabilities: Operating systems are complex software and vulnerabilities in them can have severe consequences. Patches and updates are regularly released to fix security flaws and improve system security.
Network Vulnerabilities: Networks are susceptible to various attacks, such as man-in-the-middle attacks, denial-of-service (DoS) attacks, and packet sniffing. These vulnerabilities can lead to data interception, disruption of services, or unauthorized access.
Phishing and Social Engineering: Phishing involves tricking individuals into revealing sensitive information, such as passwords or personal data, by posing as a trustworthy entity. Social engineering tactics exploit human psychology to manipulate people into disclosing confidential information or performing actions that compromise security.
Weak Authentication and Authorization: Weak or default passwords, poor password policies, and insufficient access controls can provide attackers with easy entry points into systems or sensitive data.
Insecure APIs: Application Programming Interfaces (APIs) are prone to vulnerabilities if not adequately designed and implemented. Attacks such as API injections or abuse of excessive privileges can compromise systems.
Physical Security Breaches: Physical access to devices or data centers can lead to unauthorized access or theft of sensitive information.
IoT (Internet of Things) Vulnerabilities: Devices connected to the Internet can be exploited if they lack proper security mechanisms, making them vulnerable to attacks that compromise user privacy or enable remote control by malicious actors.
Supply Chain Attacks: Hackers can compromise the software or hardware supply chain, injecting malicious code or backdoors into products before they reach end-users.
Insider Threats: Employees or individuals with privileged access to systems can intentionally or unintentionally cause security breaches or data leaks.
Key differences between Vulnerability Management, Vulnerability Scanning and Vulnerability assessment.
Vulnerability Scanning
Single Activity
Accomplished by tools (Acunetix, Nessus, Netsparker, etc.)
Automated process
Minute/Hours
The main goal is to identify vulnerabilities in assets
Vulnerability assessment
Group of multiple activities
Scanning + Assessment
Accomplished by tools and a small number of employees
Automated + Manual process
Days
The main goal is to identify legitimate vulnerabilities, and false positives, assign urgencies based on the severity and likelihood of an attack
Vulnerability Management
Program of multiple activities and processes
Accomplished by multiple tools, various cyber divisions, and multiple people
Automated + Manual
Months/Years (Continuous Program)
The main goals are to maintain an ongoing program that helps organizations on identifying and mitigating vulnerabilities in their internal and external assets by integrating multiple processes into one such as security incidents, penetration testing, Shadow IT, Open source monitoring, etc.
Common Frameworks for Vulnerability Management
"DARC" or "Detect, Assess, Remediate, Confirm" is a common framework or process used in cybersecurity and vulnerability management to address security threats and vulnerabilities. It outlines the essential steps organizations should follow to manage and respond to security incidents and vulnerabilities effectively. Let's go through each step:
Detect:
In this step, the organization employs various tools and techniques to detect security incidents, suspicious activities, and potential vulnerabilities in its systems and network.
Intrusion detection systems, antivirus software, anomaly detection, and log monitoring are some of the tools used to detect security events.
Assess:
Once a security incident or vulnerability is detected, it needs to be assessed to understand its severity and potential impact on the organization's assets and operations.
This step involves conducting a thorough investigation, analysis, and risk assessment to prioritize the response efforts.
Remediate:
After assessing the security incident or vulnerability, the organization takes actions to mitigate and remediate the threat or weakness.
Remediation may involve applying security patches, reconfiguring systems, isolating affected components, or implementing additional security controls.
Confirm:
The "Confirm" step involves verifying the effectiveness of the remediation efforts and ensuring that the vulnerability or security incident has been adequately addressed.
Organizations perform follow-up assessments and validation checks to confirm that the issue is resolved and no longer poses a threat.
The DARC framework provides a structured and systematic approach to vulnerability management. It helps organizations respond promptly and effectively to security incidents and vulnerabilities, minimizing potential damage and reducing the overall risk to the organization's assets and data.
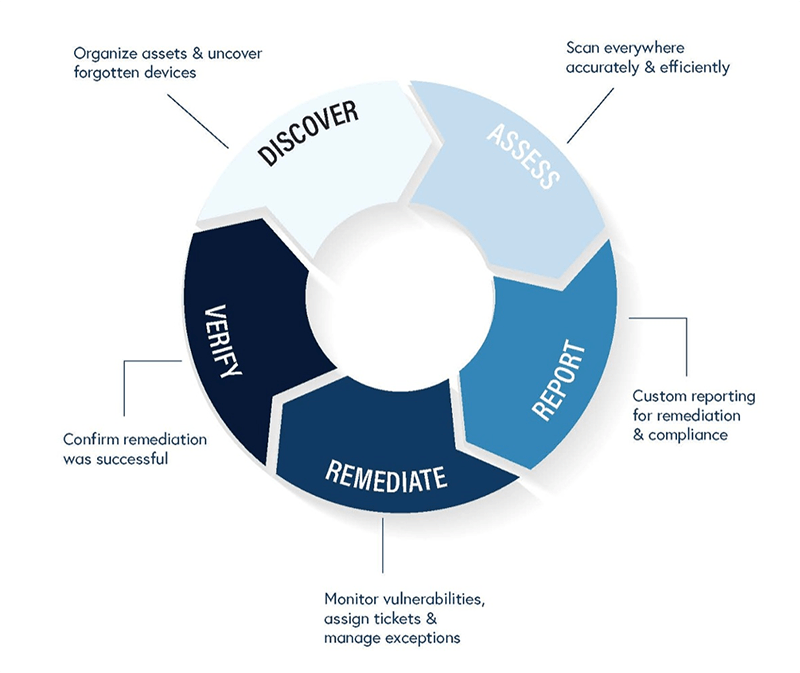
Vulnerability Management Process Steps
Preparing Inventory List
Preparing an inventory list for a Vulnerability Management program involves identifying and cataloging all assets and components within an organization's IT infrastructure.
Identify Assets and Components:
- Start by identifying all the assets and components that make up your IT infrastructure. This includes servers, workstations, laptops, network devices (routers, switches, firewalls), printers, virtual machines, cloud resources, and any other devices connected to the network.
Categorize Assets:
- Categorize the identified assets based on their role, function, and criticality to the organization's operations. For example, separate assets that store sensitive data from those that are used for general purposes.
Document Asset Details:
- For each asset, document relevant details, such as asset name, IP address, MAC address, hostname, asset owner, location, operating system, hardware specifications, and installed software.
Identify Network Segments:
- Identify and document the network segments or subnets where each asset resides. Understanding the network topology helps in planning and organizing vulnerability scanning activities efficiently.
Include Third-Party Assets:
- Don't forget to include assets and components that may be provided by third-party vendors or cloud service providers. This includes cloud servers, virtual machines, and other services hosted externally.
Asset Grouping and Tagging:
Group similar assets together based on their function or characteristics. This can aid in targeted scanning and remediation efforts.
Use tagging or labeling to categorize assets further. For example, tag assets belonging to a specific department or those in the development environment.
Maintain Updated Records:
- Keep the inventory list up to date with changes in the IT environment. Regularly review and update the asset details as new assets are added or old ones are decommissioned.
Automate Inventory Management:
- Use asset discovery tools and management systems to automate the process of maintaining the inventory list. Automated tools can help keep track of assets in real time and reduce the chances of missing any components.
Regularly Audit the Inventory:
- Conduct periodic audits of the inventory to verify that all assets are accounted for and accurately documented. This helps ensure the inventory list's integrity and reliability.
Integrate with Vulnerability Scanning Tools:
- Integrate the inventory list with vulnerability scanning tools. This helps ensure that all assets are scanned regularly, and the scanning results are accurately associated with the correct assets.
And always remember accurate and up-to-date inventory list is essential for an effective Vulnerability Management program. It provides a clear understanding of the organization's attack surface and enables targeted vulnerability assessments and remediation efforts.
Assessment
The assessment process helps prioritize remediation efforts and resource allocation. Here are the key steps involved in the assessment of identified vulnerabilities:
Gather Vulnerability Information:
- Collect detailed information about each identified vulnerability, including its name, severity rating, affected systems, and the potential consequences of exploitation.
Risk Scoring and Prioritization:
Assign a risk score or severity rating to each vulnerability based on a standardized scale. Commonly used scoring systems include the Common Vulnerability Scoring System (CVSS), which rates vulnerabilities on a scale of 0 to 10.
Prioritize vulnerabilities based on their severity scores, potential impact on the organization, and exploitability.
Contextual Assessment:
- Consider the specific context of your organization when assessing vulnerabilities. Not all vulnerabilities have the same impact for every organization. Factors such as the asset's criticality, the likelihood of an attack, and existing security controls should be taken into account.
Asset Criticality:
- Evaluate the importance of the affected asset in your organization's operations. Assets holding sensitive data, critical infrastructure, or key business functions may require immediate attention if they are vulnerable.
Threat Intelligence Integration:
- Incorporate threat intelligence data to understand if any vulnerabilities are actively being exploited in the wild. This information can influence the urgency of remediation.
Consider Compensating Controls:
- Assess whether there are compensating controls in place that mitigate the risk posed by certain vulnerabilities. For example, a vulnerability may be less critical if access to the vulnerable system is limited by other security measures.
Risk Acceptance or Mitigation:
Based on the assessment, decide whether to accept the risk associated with certain vulnerabilities temporarily or take immediate action to mitigate them.
Risk acceptance may be appropriate for certain low-severity vulnerabilities with limited impact, as long as they are regularly monitored and tracked.
Remediation Planning:
- Develop a remediation plan that outlines the order in which vulnerabilities will be addressed. Focus on high-severity vulnerabilities first, and consider dependencies and potential operational disruptions when scheduling fixes.
Coordinate with Stakeholders:
- Collaborate with relevant teams and stakeholders to communicate the assessment results and the importance of addressing high-risk vulnerabilities promptly. Make sure results are displayed on a centralized dashboard.
Report
Documentation and Reporting
- Document the assessment results, risk scores, and the planned remediation actions. Regularly generate reports to provide updates on the vulnerability status and progress in resolving identified issues.
Remediate
The remediation process is a critical phase in a Vulnerability Management program. It involves taking action to address and resolve identified vulnerabilities in an organization's IT infrastructure, systems, applications, and devices.
Prioritize Vulnerabilities:
- Based on the severity and potential impact of each vulnerability, prioritize the order in which they will be addressed. Focus on high-severity vulnerabilities first, as they pose the most significant risk to the organization.
Establish a Remediation Plan:
- Create a comprehensive remediation plan that outlines the specific steps, timelines, and responsible parties for addressing each vulnerability. The plan should be based on the prioritization done in the previous step.
Patch Management:
- If the vulnerability can be remediated through a security patch or update, apply the necessary patches to affected systems. Keep all software and applications up to date with the latest security updates.
Configuration Changes:
- Make necessary configuration changes to secure systems and applications. Address any misconfigurations or insecure settings identified during the vulnerability assessment.
Apply Workarounds and Temporary Fixes:
- In cases where a security patch is not immediately available or feasible, implement workarounds or temporary fixes to mitigate the risk until a permanent solution can be applied.
Implement Compensating Controls:
- Consider implementing compensating controls to reduce the risk posed by vulnerabilities. Compensating controls are alternative security measures that address the vulnerability's impact without directly fixing the vulnerability.
Test Remediation Actions:
- Before deploying any remediation changes to production environments, thoroughly test them in a controlled, non-production environment to ensure they do not cause unintended issues.
Communication and Collaboration:
- Maintain open communication with relevant stakeholders, including IT teams, system administrators, application owners, and business units. Collaboration is essential to coordinate remediation efforts effectively.
Document Remediation Efforts:
- Keep detailed records of all remediation actions taken, including the steps performed, results of testing, and any changes made. This documentation is valuable for future reference and audits.
Verify Remediation Success:
- After applying the remediation actions, re-scan the systems to verify that the identified vulnerabilities are adequately addressed. Confirm that the risk has been mitigated or eliminated.
- Continuous Monitoring:
- Implement continuous monitoring to ensure that remediated vulnerabilities do not reappear and that new vulnerabilities are promptly identified and addressed.
- Review and Improve the Process:
- Regularly review the effectiveness of the remediation process and update it based on lessons learned and changing security threats. Continuous improvement is essential to enhance the vulnerability management program.

Verify
Verification helps confirm that the remediation efforts were successful and that the organization's systems and data are adequately protected. Here's a guide to the verification process in a Vulnerability Management program:
Preparation:
Before verification, ensure that all remediation actions have been completed based on the remediation plan.
Gather information about the remediated vulnerabilities, including the steps taken, patches applied, configuration changes made, and any compensating controls implemented.
Re-Scanning:
Conduct a vulnerability scan on the systems or assets that were previously affected by the identified vulnerabilities.
The re-scanning process should use the same scanning tool and settings used during the initial vulnerability assessment for consistency.
Validate Remediation:
- Review the re-scan results to verify that the vulnerabilities have been remediated. The vulnerabilities should no longer appear in the scan results, indicating that the remediation actions were successful.
False Positives:
- Verify that any previously identified vulnerabilities that were determined to be false positives are appropriately labeled as such and excluded from future scans.
Verify Compensating Controls:
- For vulnerabilities where compensating controls were implemented, ensure that the controls effectively mitigate the risk posed by the vulnerability.
Thoroughness Check:
- Perform a thorough check of the systems and assets to ensure that no other security issues were introduced during the remediation process.
Testing and Validation:
- If the remediation actions involved changes to the system configurations or settings, perform testing and validation to ensure that the changes did not introduce new issues or negatively impact system functionality.
Documentation:
- Document the results of the verification process, including the list of remediated vulnerabilities, any remaining unresolved issues, and the outcomes of the validation tests.
Communication:
Communicate the results of the verification process to relevant stakeholders, such as IT teams, management, and other involved parties.
Provide clear information on the success of the remediation efforts and any additional actions that may be necessary.
Continuous Monitoring:
- Implement continuous monitoring to ensure that the remediated vulnerabilities do not reappear and that new vulnerabilities are promptly identified and addressed.
- Audit and Review:
Periodically audit and review the verification process to ensure its effectiveness and to identify areas for improvement.
Learn from past experiences and apply lessons learned to enhance the verification process over time.
By conducting thorough verification, organizations can have confidence that their vulnerability remediation efforts have been successful and that their systems are more secure against potential cyber threats.
A successful Vulnerability Management program requires collaboration and involvement from various teams and individuals across an organization. The participation of these teams helps ensure that vulnerabilities are identified, assessed, and remediated efficiently and effectively. Here are some key teams and individuals that can be part of a Vulnerability Management program:
IT Security Team:
- The IT security team plays a central role in managing the Vulnerability Management program. They are responsible for overseeing the entire process, coordinating activities, and ensuring that vulnerabilities are appropriately addressed.
IT Operations Team:
- The IT operations team manages the organization's IT infrastructure, including servers, network devices, and endpoints. They are involved in vulnerability scanning, remediation, and patch management activities.
System Administrators:
- System administrators are responsible for the day-to-day operation and maintenance of servers and systems. They play a crucial role in implementing security patches and configuration changes to address vulnerabilities.
Network Team:
- The network team is responsible for managing the organization's network infrastructure. They work closely with the IT security team to ensure that network devices are scanned for vulnerabilities and that any identified issues are remediated.
Application Development Team:
- The application development team is involved in securing and addressing vulnerabilities in custom-developed software and web applications. They play a key role in remediating vulnerabilities found in application code.
Compliance and Risk Management Team:
- The compliance and risk management team ensures that the organization adheres to industry regulations, standards, and best practices related to cybersecurity. They assess risks associated with vulnerabilities and help prioritize remediation efforts.
Information Security Officer (ISO):
- The ISO is responsible for overseeing the organization's overall information security strategy, including the Vulnerability Management program. They provide guidance, support, and resources to ensure the program's success.
Executive Management and Business Units:
Executive management should be informed about the Vulnerability Management program's progress and outcomes. They play a crucial role in allocating resources and setting priorities based on the program's recommendations.
In some cases, business units may also be involved, especially if they are responsible for specific systems or applications that need to be scanned and remediated.
Third-Party Vendors:
- If the organization uses third-party vendors for various services, it's important to collaborate with them to ensure that their systems and services are also scanned for vulnerabilities and that any identified issues are addressed.
Security Incident Response Team (if separate):
- If the organization has a separate Security Incident Response Team (SIRT), they should be involved in the Vulnerability Management program. They help assess the severity of vulnerabilities and coordinate response efforts in case of critical issues.
Thank you for reading.
